Breakdown of the GMX hack.
🧵
II. "Wait, what happened?"
On July 9, @GMX_IO V1 on the @arbitrum was hacked, and ~$40M was stolen from the GLP pool.
@GMX_IO quickly halted trading on V1 and disabled minting or redeeming GLP tokens on both @arbitrum and @avax to prevent further damage.
The GLP pool of GMX V1 on Arbitrum has experienced an exploit. Approximately $40M in tokens has been transferred from the GLP pool to an unknown wallet.
Security has always been a core priority for GMX, with the GMX smart contracts undergoing numerous audits from top security specialists. So, in this hands-on-deck moment, all core contributors are investigating how the manipulation occurred, and what vulnerability may have enabled it.
Our security partners are also deeply involved, to ensure we gain a thorough understanding of the events that occurred and minimise any associated risks as quickly as possible. Our primary focus is on recovery and pinpointing the root cause of the issue.
Actions taken:
Trading on GMX V1, and the minting and redeeming of GLP, have been disabled on both Arbitrum and Avalanche to prevent any further attack vectors and protect users from additional negative impacts.
Scope of the vulnerability:
Please note that the exploit does not affect GMX V2, its markets, or liquidity pools, nor the GMX token itself.
Based on the available information, the vulnerability is limited to GMX V1 and its GLP pool.
As soon as we have more complete and validated information, a detailed incident report will follow.
IV. Using an automated keeper (software bot), the attacker triggered numerous short orders during execution (with timelock.enableLeverage) to inflate the GLP price and then cashed out for real assets.
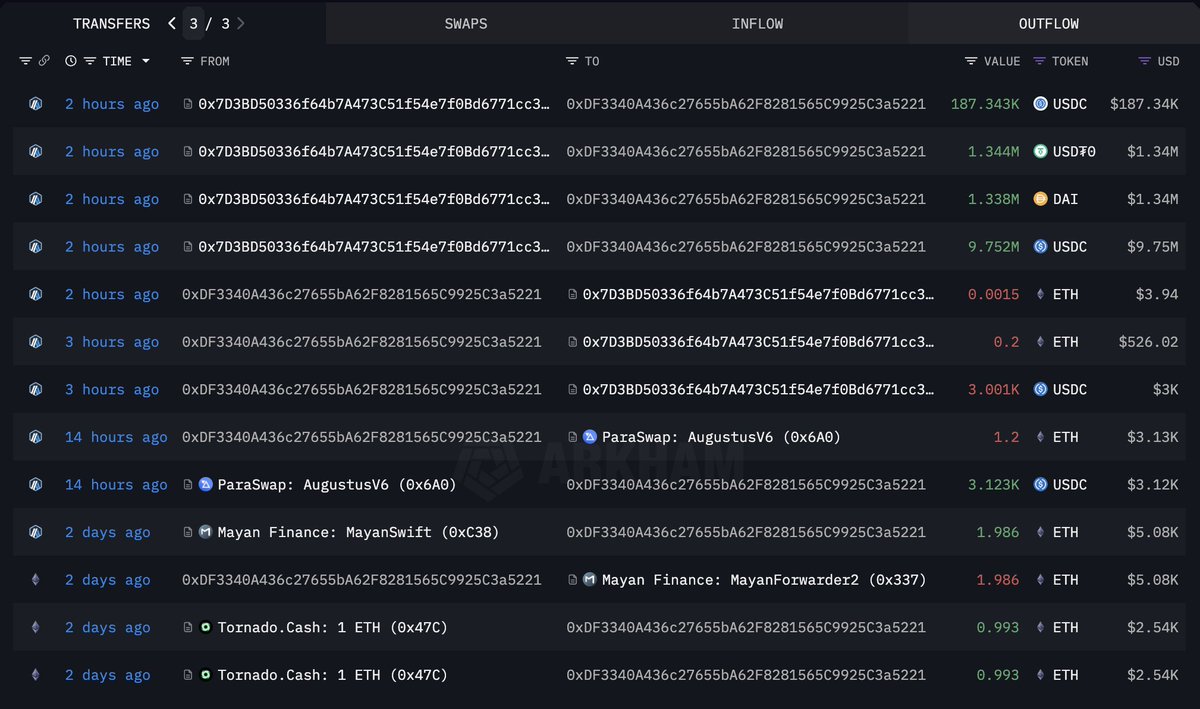
V. All stolen assets were sent to a single wallet (0xDF3340a436c27655bA62F8281565C9925C3a5221).
~$10M was bridged to @ethereum and exchanged for $ETH and $DAI; the rest (~$32M) stayed on @arbitrum in tokens like $wBTC, $FRAX, $LINK, $USDC, and $USDT.
Some of the funds were mixed through @TornadoCash.
VI. "How did the audits miss it?"
@GMX_IO V1 contracts had undergone audits from @Quantstamp and @ABDKconsulting, along with bug bounties and monitoring from @GuardianAudits.
Yet these didn't catch the protocol‑specific logic flaw involving real‑time price updates during short trades.
VII. Even audited code can fail when subtle protocol behavior isn't thoroughly tested.
VIII. "What @GMX_IO did to mitigate damage?"
Paused all V1 trading and GLP operations to prevent further exploitation.
Also, @GMX_IO offered a 10% bounty (~$4.2M) to the attacker for returning the funds promptly.
What do you, bois, think of @GMX_IO hack?
@splinter0n @0xDefiLeo @the_smart_ape @0xCheeezzyyyy @DOLAK1NG @YashasEdu @0xAndrewMoh @eli5_defi @_SmokinTed @RubiksWeb3hub @kenodnb @lstmaximalist
27.98K
61
The content on this page is provided by third parties. Unless otherwise stated, OKX is not the author of the cited article(s) and does not claim any copyright in the materials. The content is provided for informational purposes only and does not represent the views of OKX. It is not intended to be an endorsement of any kind and should not be considered investment advice or a solicitation to buy or sell digital assets. To the extent generative AI is utilized to provide summaries or other information, such AI generated content may be inaccurate or inconsistent. Please read the linked article for more details and information. OKX is not responsible for content hosted on third party sites. Digital asset holdings, including stablecoins and NFTs, involve a high degree of risk and can fluctuate greatly. You should carefully consider whether trading or holding digital assets is suitable for you in light of your financial condition.